Post Preview
Today’s increasingly mobile workforce and the rise of cloud computing have underscored the criticality of remote access solutions for businesses worldwide. Among the myriad options available, Secure Sockets Layer Virtual Private Network or SSL VPN stands out as a favorable choice for organizations aiming to equip their personnel with secure, remote access to networked resources. By leveraging the ubiquitous SSL/TLS protocol, SSL VPNs simplify the implementation of remote access while maintaining robust security. This article explores the mechanics, typologies, benefits, and insights into selecting an SSL VPN solution, guiding you to enhance your organization’s cybersecurity posture. We’ll also examine the latest developments in SSL VPNs, shaping their position in cybersecurity.
Key Takeaways:
- SSL VPNs empower users to access private network resources securely via a web browser, eliminating the complexities of specialized software installations.
- Distinguishing the two principal variants of SSL VPN—the portal and the tunnel—is critical to deploying the right fit for an organization’s specific access requirements.
- Awareness of the common security challenges inherent to SSL VPNs is crucial, and adopting security best practices ensures a robust defense strategy.
Table of Contents:
- The Mechanics of SSL VPNs
- Types of SSL VPNs
- Benefits of Using SSL VPNs for Remote Access
- Comparing SSL VPN to Other VPN Technologies
- Implementing SSL VPNs: Best Practices
- Security Concerns with SSL VPNs
- Future of SSL VPNs in Cybersecurity
- Selecting an SSL VPN Provider: What to Look For
The Mechanics of SSL VPNs
At its core, an SSL VPN is a type of VPN that provides secure and remote access to an internal network over the Internet. Leveraging the Secure Sockets Layer (SSL) protocol—which has become the de-facto standard for secure web transactions—SSL VPNs create an encrypted connection between the user’s device and the corporate network. This encrypted tunnel shields all transferred data from unauthorized access, ensuring privacy and integrity. With SSL’s evolution to the more secure Transport Layer Security (TLS), SSL VPNs continue reinforcing their encryption mechanisms, thus fostering a resilient and trustworthy link for remote users.
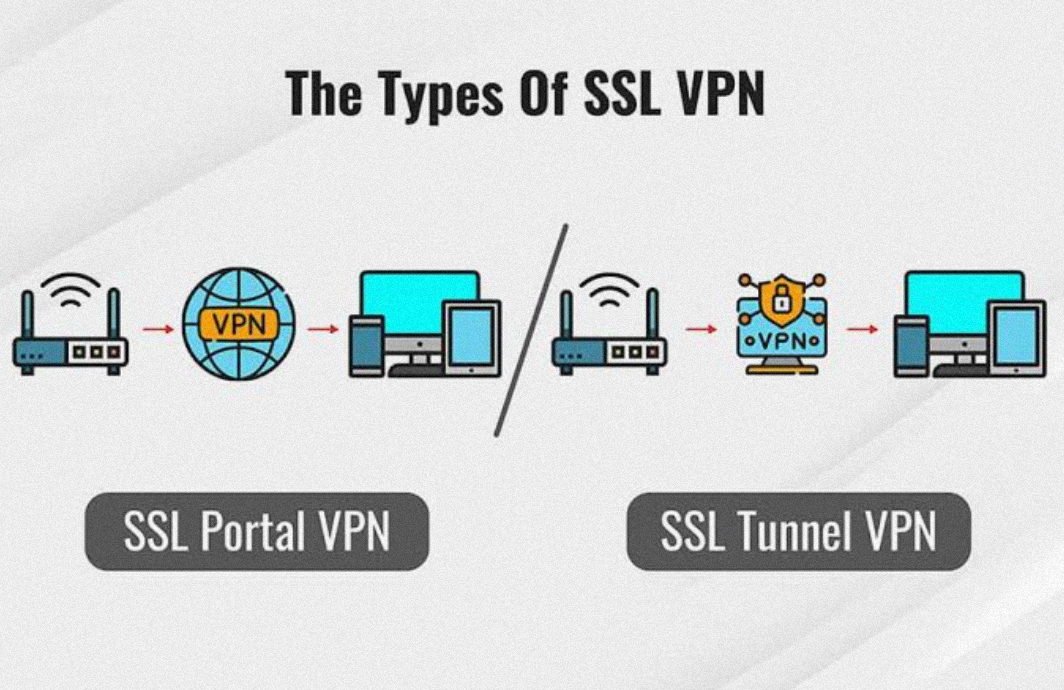
Types of SSL VPNs
There’s a remarkable utility to the various flavors of SSL VPNs currently in the arsenal of cybersecurity tools. SSL Portal VPNs deliver a single gateway to multiple services through a convenient web interface, simplifying the user experience. Individuals log in to a secure web page and can access network resources discretely presented within that portal. In contrast, SSL Tunnel VPNs offer a more comprehensive solution by creating a secure tunnel capable of transmitting a broader range of traffic than web-based ones. This allows applications and protocols not natively supported by web browsers to harness the benefits of SSL encryption. Adopting either variant should be a well-considered decision based on a nuanced understanding of organizational needs and user workflows.
Benefits of Using SSL VPNs for Remote Access
The deployment of SSL VPNs offers distinct advantages, particularly for their potential to facilitate secure, remote access without cumbersome software installations. Users can initiate secure sessions effortlessly by navigating to a URL from their preferred web browser, entering their authentication details, and launching into their remote work environment. The versatility and user-friendliness of SSL VPNs save time and resources for both the IT department and end-users. Moreover, SSL VPNs deliver a heightened level of encryption comparable to the best in the industry. These capabilities ensure user information remains safeguarded even when accessing sensitive data over less secure networks, such as public Wi-Fi.
Comparing SSL VPN to Other VPN Technologies
In the realm of VPN technologies, SSL VPNs are often juxtaposed with other protocols, particularly IPsec. IPsec VPNs excel in creating stable, permanent connections ideal for fixed site-to-site communication. However, the flexibility offered by SSL VPNs is unmatched when it comes to facilitating on-the-go, remote user access. This adaptability complements the dynamic nature of modern business practices and reduces the burden on users to install and troubleshoot client software on their devices.
Implementing SSL VPNs: Best Practices
When incorporating SSL VPN into your network’s infrastructure, it’s advisable to account for best practices from the get-go. A comprehensive implementation strategy should include:
- Consideration of user access levels.
- Integration with other security measures.
- A thorough assessment of compatibility with existing systems.
Meticulous planning and foresight can prevent unexpected challenges, paving the way for a seamless deployment that harmonizes with the organization’s security framework.
Security Concerns with SSL VPNs
While SSL VPNs have carved a niche in secure remote access, they are not wholly impervious to the evolving landscape of cyber threats. Common vulnerabilities can reside in outdated software versions, misconfigured servers, or inadequate user authentication practices. Addressing these pitfalls requires continuously updating SSL VPN software, rigorous access controls, and frequent security audits. As reportedly rising cyber threats rigorously test the mettle of security systems, the diligence in upholding SSL VPN defenses becomes all the more crucial.
Future of SSL VPNs in Cybersecurity
Innovation is synonymous with the future of SSL VPNs in the cybersecurity sphere. Providers adapt to emerging threat vectors by incorporating state-of-the-art functionalities like multi-factor authentication and endpoint compliance checks. These enhancements respond to a marketplace that demands robust security without compromising user convenience or enterprise productivity. As digital threats burgeon, the importance of forward-looking VPN technologies like SSL VPN gains traction—solidifying their role in cybersecurity for years to come.
Selecting an SSL VPN Provider: What to Look For
Identifying the most suitable SSL VPN provider is a strategic venture that should be handled with circumspection. Look for solutions that offer comprehensive security features, support a diverse range of devices, and tout an intuitive user interface. For organizations anticipating growth, scalability becomes a pivotal consideration—as is the presence of an attentive customer support team. With these criteria at the forefront, businesses can select a provider that meets their current needs and is a viable partner as they evolve and expand.
In our accelerated digital world, the significance of secure remote access solutions like SSL VPNs continues to burgeon. They are becoming an indispensable component of the cybersecurity toolkit for a growing cadre of companies. This deep dive into SSL VPNs serves as a strategic blueprint for organizations seeking to leverage secure, remote access while safeguarding against the omnipresent cyber dangers.