The Evolution of Network Security and the Rise of SASE
In the past decade, network security has taken center stage in IT discussions, predominantly due to the widespread adoption of cloud services and the increase in mobile workforces. Traditional network architectures, designed for a pre-cloud era, began showing their limitations, needing help to efficiently deal with the high demands of security and performance posed by modern enterprises. The Secure Access Service Edge (SASE) concept was born in response to this challenging landscape. SASE is a transformative approach that answers the question of what is SASE? by unifying advanced network security measures with the extensive reach of WAN services, aiming to support the dynamically secure access needs of organizations across the globe.
Understanding SASE
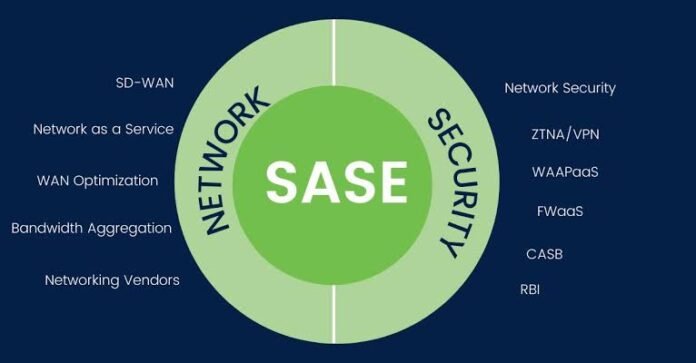
SASE’s innovativeness continues beyond its capabilities. It also shifts the locus of networking and security from on-premises hardware to the cloud, allowing users to access the resources they need from anywhere securely. As a framework that integrates network security services with WAN capabilities, SASE provides a holistic approach that has caused a paradigm shift, propelling network security into a new realm of possibilities and challenges.
Demystifying SASE: What It Is and How It Works
SASE, pronounced “sassy,” is often heralded as a cloud-native leap forward in the convergence of security and network technologies. It is designed to deliver a comprehensive and agile solution that meets the networking needs of enterprises. SASE is a collection of various network and security technologies encompassing capabilities such as real-time threat prevention, data protection, and secure access, all delivered through a single, integrated cloud service. This amalgamation aims to address the diverse and ever-increasing security concerns inherent in today’s highly mobile and cloud-centric workforce by providing consistent, low-latency security regardless of a user’s location or the resources they’re accessing.
The Benefits of Integrating SASE into Your Network Infrastructure
The decision to transition to a SASE framework is often motivated by the promise of remarkable benefits that align closely with the strategic goals of modern enterprises. One of the paramount benefits of SASE is its ability to provide next-generation security measures directly from the cloud. It lends itself to a more secure environment as security policies can be uniformly applied to all network traffic without discrimination. The centralization of such policies plays a pivotal role in simplifying security oversight and reducing the risk of breaches.
- Scalability: Unlike traditional security models, SASE is inherently scalable and can dynamically adapt to the ebb and flow of an organization’s operations without additional hardware.
- Cost-Efficiency: By consolidating security services into the cloud, SASE architectures can reduce an enterprise’s reliance on costly physical hardware and legacy systems, thus driving down capital expenses traditionally associated with maintaining and scaling network security solutions.
- Performance: SASE architectures enable a direct-to-cloud connection model that often reduces latency compared to traditional data center-centric networks. Improved performance and speed, as experienced through SASE’s cloud-native framework, can significantly enhance the end-user experience, a critical factor for maintaining productivity in distributed teams.
How SASE Contributes to Streamlined IT Operations
The all-encompassing nature of SASE holds significant implications for IT operations. Its integrated design combines various networking and security functions typically dispersed across multiple products. This level of integration reduces vendor complexity, easing the burden on IT teams. Consolidating services under SASE eliminates the need for disparate management consoles and varying policy paradigms, resulting in cohesive policy enforcement and simplified operational processes. It enables IT teams to focus more on strategic initiatives rather than being entangled in maintaining a multifaceted stack of security products.
SASE in Action
Firms that have leveraged SASE report improved agility owing to the ease with which security policies can be updated and enforced in real-time across all access points. It is precious in an era where workforces are distributed and network perimeters are borderless. SASE’s centralized approach enhances security and offers a clear roadmap for the future, aligning with the overarching trend of cloud and as-a-service models.
Case Studies: SASE Implementation and Organizational Impact
Anecdotal evidence from various industry sectors points to SASE as a keystone for modern secure networking. Organizations transitioning to remote work models have found SASE invaluable in facilitating robust, safe, high-speed access to corporate tools and data. Metrics such as reduced operational overhead, lower total cost of ownership, and notable decrease in security incidents post-implementation underscore the tangible impact of SASE-based transformations.
Planning for SASE: Key Considerations and Best Practices
Transitioning to a SASE framework is not a one-size-fits-all process. Considering the existing networking and security architectures, it should be tailored to a firm’s particular needs. A critical first step is to conduct thorough assessments that measure the current state against the desired outcomes. As a best practice, enterprises should aim to understand their traffic patterns, scrutinize security policies, and anticipate how introducing SASE could impact them. Iterative implementation, starting with smaller pilot projects to hone in on specific benefits and risks, is also a widely recommended approach for SASE adoption.
SASE Deployment Strategy
Planning for SASE adoption should be meticulous, with close consideration of organizational objectives. It might involve mapping out a complete overhaul of the existing network infrastructure or more incremental changes that build upon and integrate with current assets. The goal is to establish a purpose-driven, realistic roadmap that can be executed with minimal disruption to business continuity. Establishing clear migration strategies to SASE that are aligned with expert insights can help navigate the complexities and reap the intended benefits.
Future Outlook: The Continuing Advances in SASE and Network Security
As organizations continue to evolve and digitization of the workplace becomes more profound, SASE is set to play a critical role in the overarching network security strategy. The industry expects continuous advancements in SASE technologies, with developments in machine learning and artificial intelligence likely to make these systems even more intelligent and autonomous in neutralizing threats. The agility and adaptability provided by SASE position it as an enduring element in the armory against growing cyber threats. Observers and strategists agree that SASE is well on its way to becoming an integral part of the network security blueprint for forward-thinking organizations.